In-person direct access is what is often required to be able to get a complete view of what happened, because some of the data doesn’t show when you’re just looking at the produced printed charts. Such missing items may include: routing history, what the notes look like at different points in time, access to inactive or deleted records, and communications. Below is a screenshot from a popular Health Information System, Epic.
EPIC
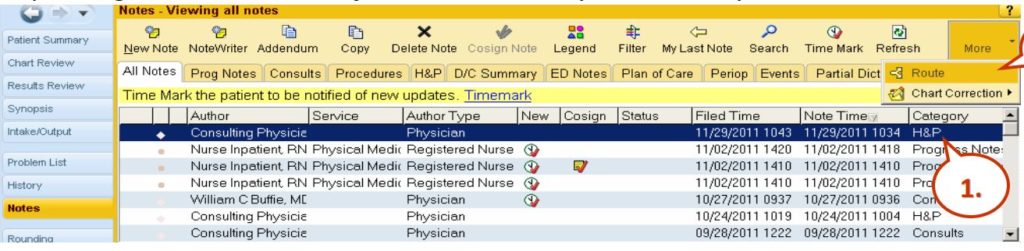
So this is Epic and here you see the notes view and when you’re entering into the system, there’s routing which can give you additional detail about what happened in terms of the routing of the notes. You have a note time, a filed time, and a note time. In this case, all these records with exception of this one down here, the 10:04 AM note time was filed 15 minutes later. So it’s important to have both date and timestamps because sometimes, the file times are many days after discharge or nowhere contemporaneously to the events and that’s important if notes are being entered into this EMR days after something awful happened, you really want to know when those notes were filed. If they’re filed long after things went wrong, oftentimes, that suggests that fabrication of the EMR took place. You can see here, here’s some of the routing, it allows for you to specify different recipients and so knowing that routing of information, that’s important because it’s not always evident when you’re looking at the chart. Here’s an example of adding a note and you can see here, there’s the ability to copy and paste different notations. The date and time on these notes when you first go to create a note, default to the current computer’s clock time but it’s totally possible to change the date and time to put it back in time by dates or hours and that information is relevant. Here’s an example of the Cerner notes. Again, Cerner allows the user to change the date to something other than the current date and time. And it still stores, again, the creation time of that note, even if the note purports to be days earlier. And there are also different filters here, when you’re looking at the EMR with power notes on Cerner, there are different filters, such as my notes only, there’s inactive, active, and so on.
Watch other videos making up this 4 part series, Unlocking the EMR Audit Trail.
| Part 1 of 4: “The Keys to Unlocking Electronic Medical Records” https://enigmaforensics.com/blog/keys-to-unlocking-the-emr-audit-trails-electronic-medical-records/ |
| Part 2 of 4: “HIPAA” https://enigmaforensics.com/blog/health-insurance-portability-and-accountability-act-of-1996-hipaa/ |
| Part 3 of 4: “Navigating to Trial or Settlement” https://enigmaforensics.com/blog/navigating-to-trial-or-settlement/ |
| Part 4 of 4: “In-Person Direct Access” https://enigmaforensics.com/blog/in-person-direct-access-provides-additional-information/ |


