Smash and grab is no longer required to open a motor vehicle and drive off.
Vehicle theft over the years has largely been on the decline. Technology has improved, therefore, Anti-Theft Systems have gotten more advanced. Beginning around 1983, keyless entry systems began appearing on American Motors vehicles. By the mid to late 2000s, many fobs enabling remote ignition start became more common place on higher end vehicles. However, as this technology advances, criminals are finding new ways to break through.
Security researchers first reported security vulnerabilities in motor vehicle fobs around 2016. This could allow an unauthorized person to unlock and even start a vehicle by intercepting radio frequency (“RF”) emissions from a driver’s fob. Once intercepted, the unauthorized party could use the intercepted signals to conduct a replay attack. As a result, a successful attack on these identified vulnerabilities can allow the unauthorized person to unlock and start a vehicle.
RF Relay Attack Reported in 2017
On November 28, 2017, Police in West Midlands, UK released video footage showing criminals stealing a car by relaying a signal from the fob key inside the home to the car in the driveway. This fob replay attack effectively allows thieves to unlock a vehicle and start the ignition then are able to drive off with the vehicle undamaged. Later on, the thieves swap out the VINs, and reprogram new key fobs to work with the stolen vehicle.
Defcon Cyber Security and Hacker Conference Focus on Vehicle Exploitation in 2018
In 2018, Defcon, a popular cybersecurity event, attended by black and white hat hackers, featured its first Car Hacking Village. During that convention, a good deal of technology related vulnerabilities on vehicles were shared. Both White and Black Hat hackers attend these events. The Black Hats are the bad guys that seek to use security vulnerabilities to exploit weaknesses and commit crimes.
Motor Vehicle Theft Jumps in 2020
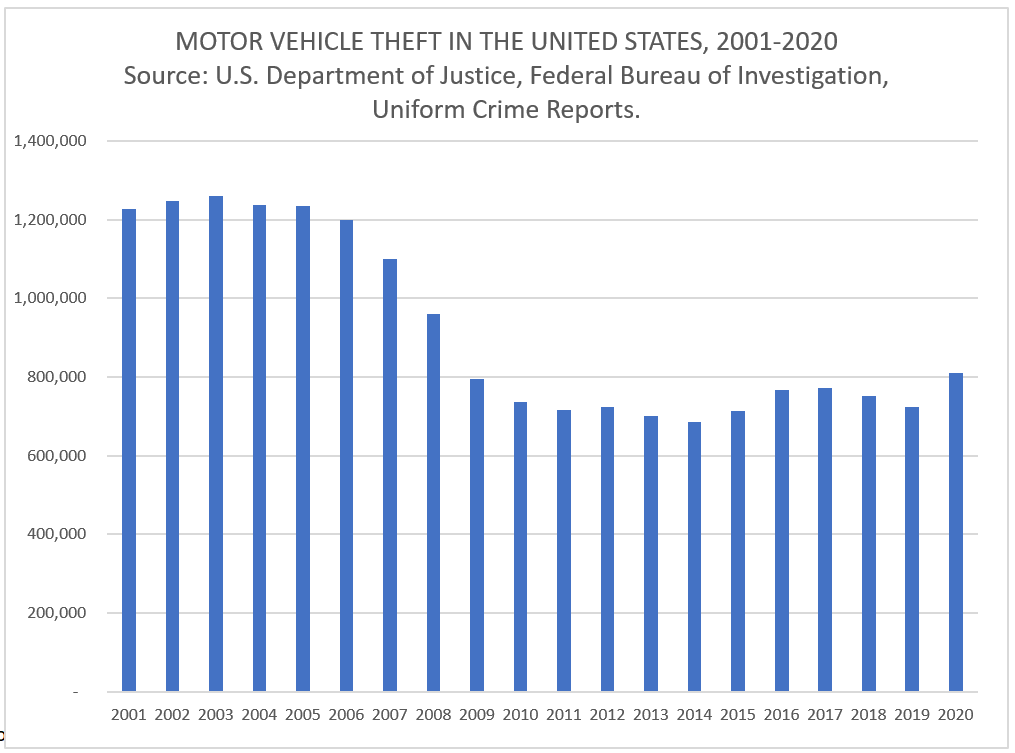
Motor Vehicle Theft data sets have yet to be released for 2021 for the entire United States. Early indicators show these types of crimes are experiencing rapid growth across the US.
High end vehicles are more likely to have keyless entry and remote ignition starting capabilities. They can also fetch a higher dollar amount when resold outside the US. As a result, according to New Jersey state police officer Cory Rodriguez, “Car theft in 2021 is up over 21% year-to-date for total thefts and about 44% for high-end vehicles.” Reports have indicated that thieves are using technology to execute vehicle thefts more efficiently and without immediate detection.
Chicago Motor Vehicle Thefts Climb with Fewer Arrests Made in 2021
Chicago Police Officers have witnessed thieves using laptops and other cyber tools to accelerate their ability to quickly steal locked vehicles. Data compiled from the City of Chicago website shows that “Motor Vehicle Thefts” across the city are accelerating at an alarming rate. The problem isn’t specific to Chicago and vehicle thefts appears to be increasing across the country as well.
In Chicago, February 2021 crime statistics reported a total of 627 Motor Vehicle Theft incident reports filed. Of those reports, only 26 (4.1%) resulted in an arrest. Comparatively, last month in January 2022, there were 1,073 Motor Vehicle Theft related police reports filed, with only 20 (1.8%) of those resulting in an arrest.
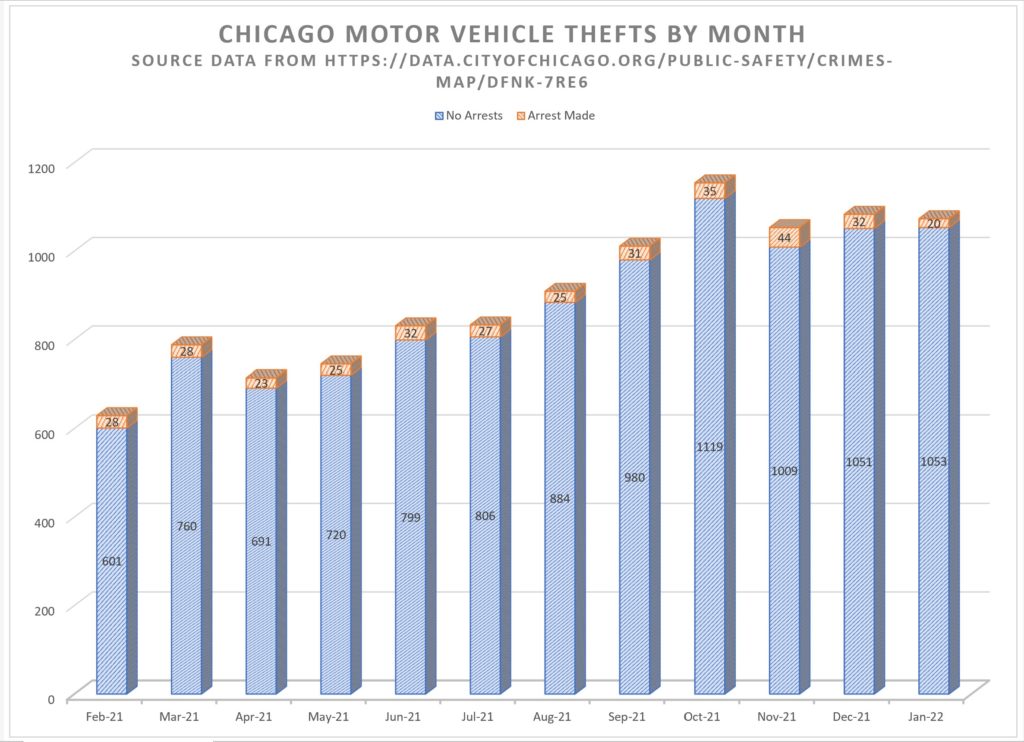
Our data analysis of Chicago Crime statistics for the 12 month period beginning February 2021 until January 2022 indicates that there were a total of 10,823. Motor Vehicle Theft incidents reported. This equates to 395 per 100,000 persons based on Chicago’s 2021 estimated population of 2,739,797.
Vehicle thefts on the rise throughout the USA
Vehicle theft isn’t just rising in Chicago. In fact, Chicago doesn’t even rank among the top 20 US cities in vehicle thefts. For example, California, Texas and Florida are continually among the top states in vehicle theft per capita. Bakersfield, California has been the top city in vehicle thefts since 2019 and in the top 10 even longer. The rate of vehicle theft went up almost 25% from 2019 in Bakersfield in 2020.
Other cities are following similar trends. For instance, San Francisco’s rates rose almost 27% while Seattle’s rose almost 26% from 2019 to 2020. Additionally, the city with one of the largest 2019 to 2020 changes being Denver, which rose over 50%.
Conclusion
Above all, it’s important to remain cautious with your vehicle. Furthermore, there are steps you can take to help ensure your vehicle doesn’t get stolen and recovery steps for your vehicles safe return if it does. Despite the overwhelming decrease in motor vehicle thefts throughout the years, this recent upward reversal of the historical trend should be alarming to vehicle owners everywhere.
(Denver statistics filtered for reports coded as any of the following; “burg-auto-theft-busn-no-force”, “burg-auto-theft-busn-w-force”, “burg-auto-theft-resd-no-force”, “burg-auto-theft-resd-w-force”, “robbery-car-jacking “, “theft-items-from-vehicle”, and “theft-of-motor-vehicle”)
California, Texas and Florida lead the states with the greatest number of vehicle thefts and accounted for 37% of all Motor Vehicle Thefts in the nation, based on 2020 National Insurance Crime Bureau statistics.